[ad_1]
Advert

The race for WEB3 has begun. Enterprise capitalists, cryptocurrency startups, engineers, and visionaries are creating WEB3 (or Internet 3.0) powered by blockchain. A brand new frontier arose, extra democratic, decentralized, unbiased, and perfect for information restoration.
However is every little thing so good relating to decentralization and safety of infrastructures? No, and quite a few instances of man-in-the-middle assaults are proof of that.
However to unravel the safety subject, let’s keep in mind what WEB3 is. The core idea of WEB3 is to unravel the safety issues attributable to centralization and to offer folks with authority over their information and identification. So at what degree of know-how are these unlucky incidents of safety breaches occurring in your blockchain infrastructure? Let’s determine it out.
To deal with the interior features of WEB3, applied sciences equivalent to EVM, Solidity, and JavaScript nonetheless play a large function. Nonetheless, we use Node suppliers and WEB3 API suppliers when discussing backend options.
Node suppliers are corporations that let you use their companies as an alternative of operating your nodes. That is very handy as a result of as an alternative of organising your node and experiencing all of the stress and expense that comes with it, you’ll be able to ship your dApp transaction requests over the Web to the node supplier. If you happen to’re focused on good contract growth, you might use one or two node suppliers (for redundancy).
There are lots of WEB3 API suppliers; nevertheless, in lots of situations, these corporations work with nodes behind the scenes. With these instruments utilized, you may get any pre-compiled and pre-computed information on the chain.
Furthermore, it’s easy to determine dependable communication and interplay between totally different purposes via these WEB3 APIs. As well as, high quality APIs maintain coding constant and steady. We, subsequently, depend on reliable WEB3 APIs essentially the most when creating purposes.
? Distinction between Node suppliers and WEB3 API suppliers: WEB3 supplier permits your utility to speak with a blockchain node by submitting JSON-RPC requests to a server. Node service suppliers run distributed node shoppers behind the scenes and allow them to write to and skim from a blockchain utilizing an API key.
What’s the safety risk for dApps builders?
Nodes are nonetheless comparatively primitive applied sciences, however they’re nonetheless beneficial. For instance, a WEB3 node can’t let you know what customers have deposited of their accounts. Apart from merely offering uncooked blockchain info, nodes can’t course of a number of good contracts. Moreover, nodes have restricted capabilities and might solely course of one chain. Happily, there are APIs out there that can assist you circumvent this limitation.
APIs outline and standardize purposes’ interactions, permitting you to make use of uncooked blockchain information. For this reason WEB3 APIs are useful for dApp growth. WEB3 APIs are a key element within the growth of dApps; along with providing a easy interface, they permit a chunk of software program to work together with different purposes. As a result of dependable APIs enable for constant coding in a steady surroundings, dApp builders don’t must reinvent the wheel.
Moreover, by utilizing these WEB3 supplier APIs, you’ll be able to simply hyperlink to nodes. Due to this fact, you would not have to fret about connecting to nodes when utilizing these APIs. When interacting with these suppliers, you may additionally obtain all kinds of beneficial precalculated and precompiled on-chain information.
However such companies don’t solely shut builders’ requests within the safety plans, and generally, it’s a must to pay upfront for his or her use.
The very fact is that there are increasingly more instances of dApps being hacked utilizing the man-in-the-middle assault we talked about above.
That is when an attacker, utilizing vulnerabilities in DNS servers (for instance), switched servers to serve jsonrpc-endpoints visitors.
One sufferer is thought to have misplaced 16.5 WBTC (~$350,840). And about 23 cryptocurrency initiatives have already encountered an identical DNS assault.
A quite simple answer permits you to defend your self from such man-in-the-middle assaults. And we are going to return to this.
Additionally, if in case you have a growth crew, you’ll be able to go your personal manner and attempt to construct your answer, however you want a super-skilled crew of like-minded folks to make it work.
The problem of this course of is which you could considerably overestimate your power. A process that appears simple then raises many questions, that are solved by a few years of expertise in a single’s work. Due to this fact, if in case you have a number of time and assets, you must settle for this path.
Violation of three fundamental blockchain rules within the WEB3
So let’s take a breath now and have a look at the present safety challenges within the WEB3 world from an infrastructure perspective.
The principle rules of blockchain are
decentralizationtransparencytrustlessness
However does it work in observe? Check out the hottest dApp structure.
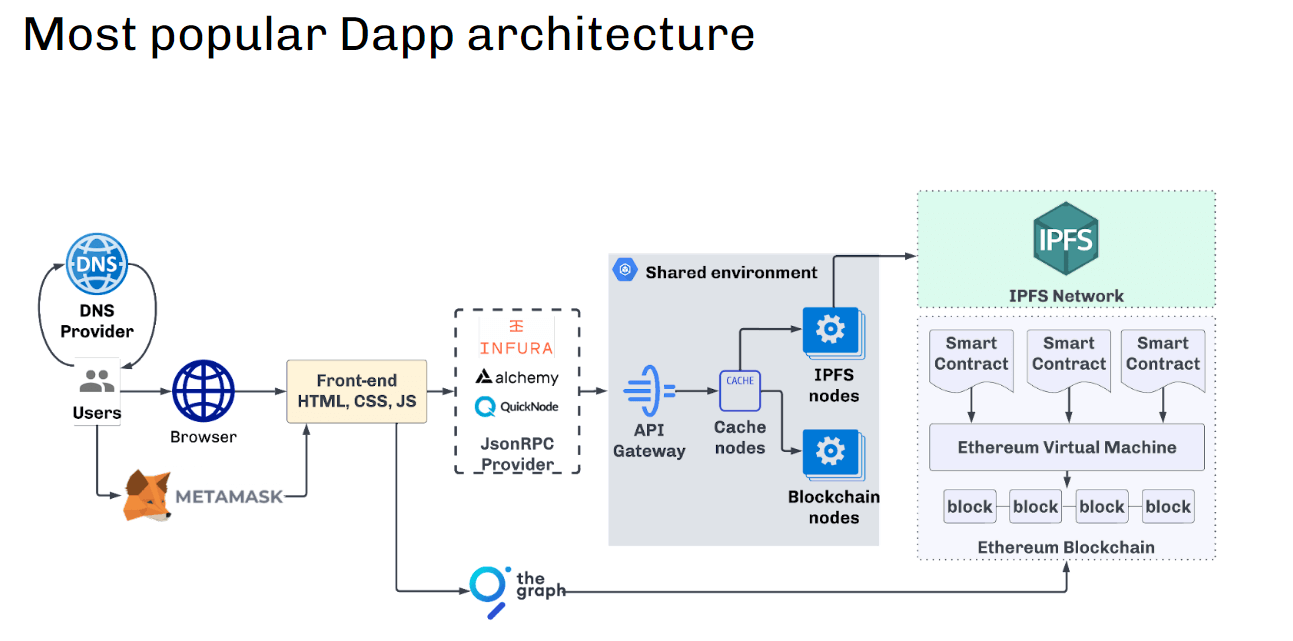
 We will see that customers on the entrance finish are sending requests to JSON-RPC suppliers (this may very well be Infura, Alchemy, Quicknode, and so on.).
We will see that customers on the entrance finish are sending requests to JSON-RPC suppliers (this may very well be Infura, Alchemy, Quicknode, and so on.).
So the requests are routed to a shared surroundings the place now we have no management over the info transformation on the API gateway, caching engine, blockchain nodes, or the rest.
And that is the place the primary downside arises as a result of a shared surroundings implies that many customers, bots, and hackers, particularly, work in the identical surroundings. It is a actual black field for the developer that draws an excessive amount of consideration from attackers.
Nicely, this method contradicts all 3 rules of WEB3 as a result of:
It centralizes entry to the Blockchain, passing every little thing via a shared surroundings;It isn’t clear—we can’t confirm responses from such an API;Due to this fact, it can’t be known as true distrust because the safety problems with such an infrastructure are based mostly merely on belief. See for your self within the following diagram.
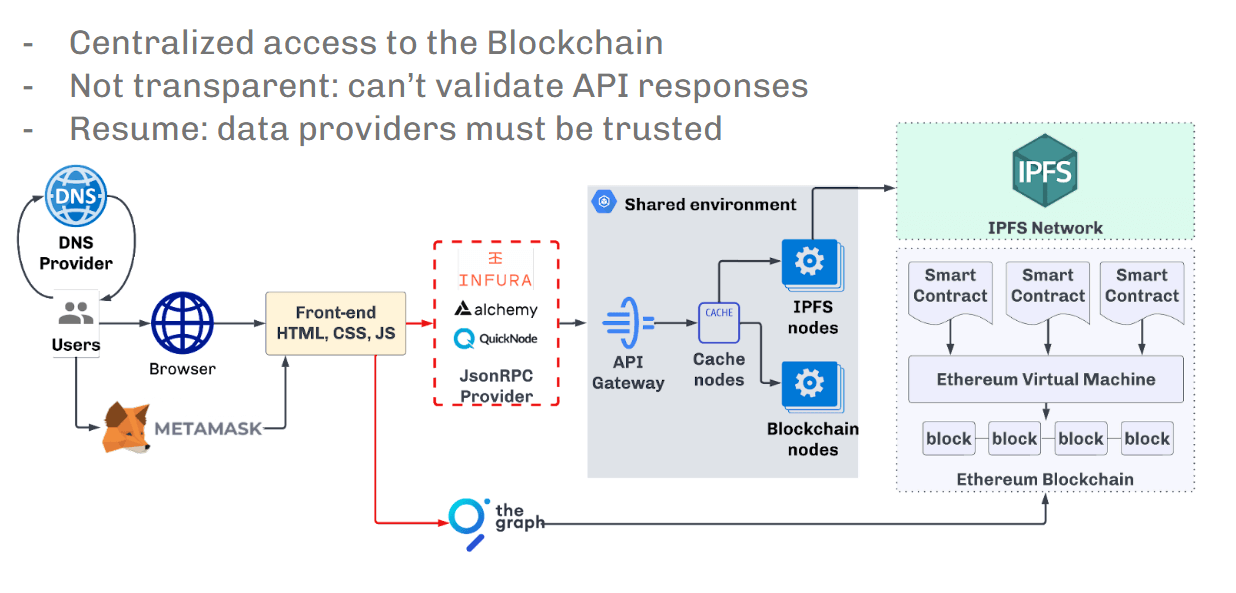
 The second subject is that the described infrastructure model permits for man-in-the-middle assaults, which criminals periodically use.
The second subject is that the described infrastructure model permits for man-in-the-middle assaults, which criminals periodically use.
The next companies will be attacked:
Area or DNS registrarsJSON-RPC suppliersAny third-party aggregated companies
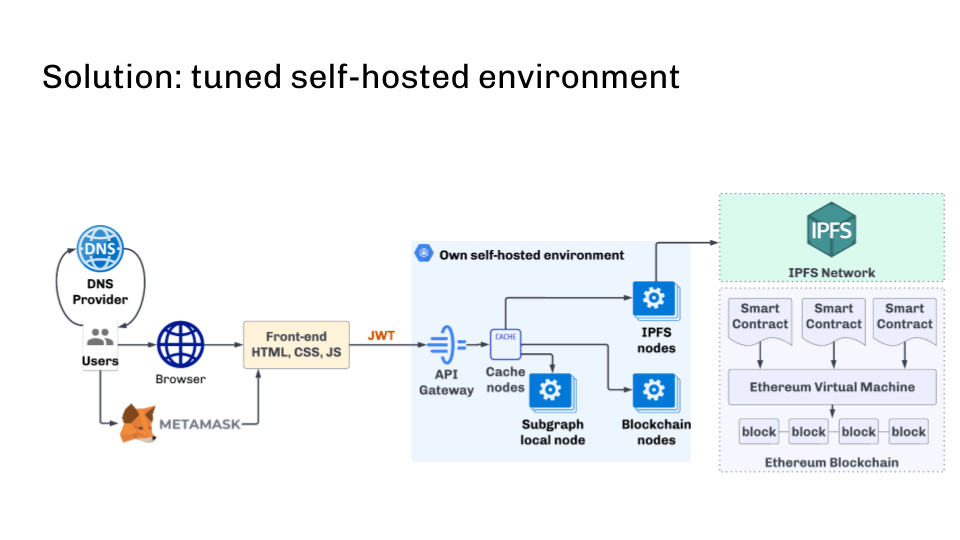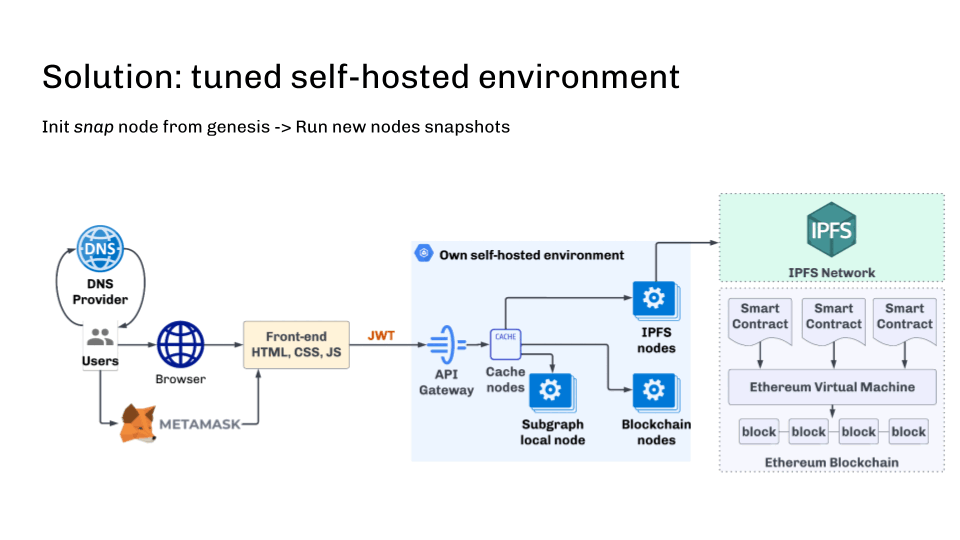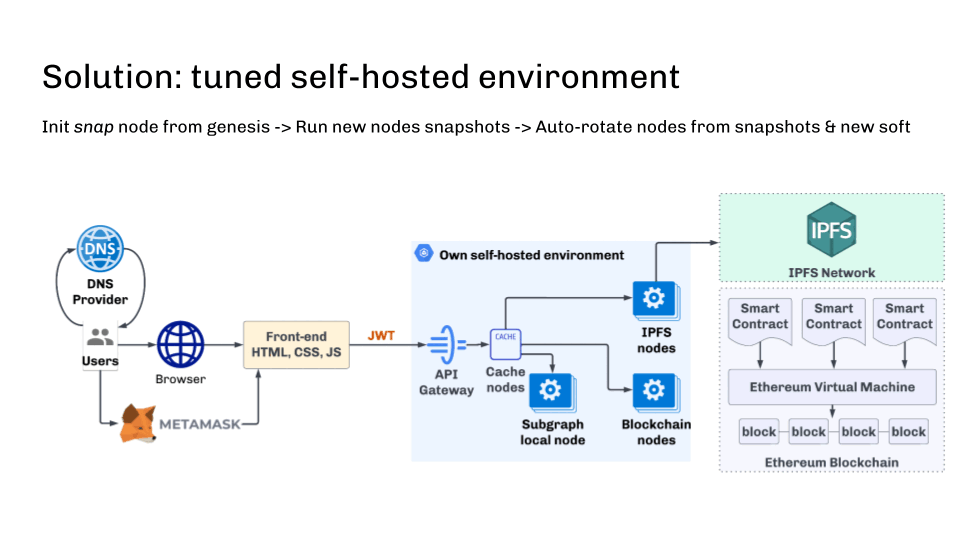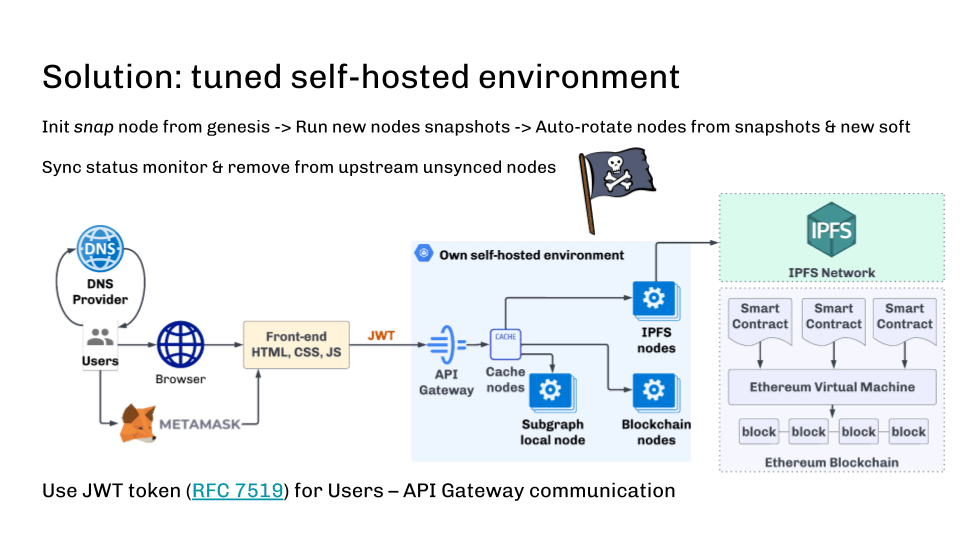
A self-hosted cluster of blockchain nodes is the one answer
However is there an answer? Sure — configured on-prem surroundings.
First, it makes use of a self-hosted cluster of blockchain nodes. All nodes are initialized from official genesis and synchronized utilizing p2p. This ensures information consistency.
Nodes ought to be up to date periodically with diminished snapshots to run as effectively as doable. The perfect answer is robotically creating new nodes from the diminished snapshot when zooming. If you happen to initialize the node from scratch, this method permits you to get a brand new node inside half-hour as an alternative of a number of days.
One other essential level is the automated replace of the blockchain software program after its launch—this can be performed. The principle factor is to create a snapshot with the brand new model (as typically it could require some information operations, which may take time), after which the brand new nodes ought to begin robotically with the brand new snapshot and up to date software program.
Under is an infrastructure diagram that solves many of the described issues.
It’s also vital to observe the synchronization state and exclude these nodes which are behind the upstream stream. This may be performed, for instance, with the assistance of well being checks.
Along with the truth that entry will be restricted by IP deal with, it’s value mentioning that the great outdated JWT token can defend in opposition to area registrar or DNS assaults. JWT token is well built-in into web3js and different libraries and ought to be applied on the API gateway aspect in our blockchain cluster.
On this manner, we make the blockchain endpoint safe and decentralized.
Summing up
Web3 remains to be in its early levels. However the race for decentralization is already on. And it is possible for you to to see that essentially the most safe purposes are prone to be those that use essentially the most revolutionary and open-source approaches.
And subsequently, you shouldn’t ignore the essential rules of WEB3 as a result of then your newly created dApp is not going to present safety to different contributors. The one possibility presently out there is an autonomous cluster of geo-distributed blockchain nodes.
Creator:
Daniel Yavorovych
Co-Founder & CTO at RPCFast and Dysnix

[ad_2]
Source link







